- Citrix Workspace Single Sign On
- Okta Remember Me
- Okta Citrix Cloud
- Okta Saas
- Citrix Cloud Gateway As Idp
- Citrix Cloud And Okta
Okta used as IDP to SAML to Citrix XenApp and XenDesktop. Enter your email address and we will send a password reset link.
Citrix ADC sends a SAML request to Okta. In this initial sequence, the Citrix ADC is acting as a SAML Service Provider (SP) and Okta is acting as an Identity Provider (IdP). The user is redirected to the Okta login page and authenticates with their sAMAccountName.
downloadWhy can't I download this file?
# Change this value for your Store
$storeVirtualPath = '/Citrix/Store1'
$auth = Get-STFAuthenticationService -Store (Get-STFStoreService -VirtualPath $storeVirtualPath)
$spId = $auth.AuthenticationSettings['samlForms'].SamlSettings.ServiceProvider.Uri.AbsoluteUri
$acs = New-Object System.Uri $auth.Routing.HostbaseUrl, ($auth.VirtualPath + '/SamlForms/AssertionConsumerService')
$md = New-Object System.Uri $auth.Routing.HostbaseUrl, ($auth.VirtualPath + '/SamlForms/ServiceProvider/Metadata')
$samlTest = New-Object System.Uri $auth.Routing.HostbaseUrl, ($auth.VirtualPath + '/SamlTest')
Write-Host 'SAML Service Provider information:
Service Provider ID: $spId
Assertion Consumer Service: $acs
Metadata: $md
 The sample output of the above command looks like this.
The sample output of the above command looks like this.
SAML Service Provider information:
Service Provider ID: https://storefront.example.com/Citrix/StoreAuth
Assertion Consumer Service: https://storefront.example.com/Citrix/StoreAuth/SamlForms/AssertionConsumerService
Metadata: https://storefront.example.com/Citrix/StoreAuth/SamlForms/ServiceProvider/Metadata
Test Page: https://storefront.example.com/Citrix/StoreAuth/SamlTest
Okta Configuration:
Note:
Storefront Configuration:
Get-Module 'Citrix.StoreFront*' -ListAvailable | Import-Module
# Remember to change this with the virtual path of your Store.
$StoreVirtualPath = '/Citrix/Store'
$store = Get-STFStoreService -VirtualPath $StoreVirtualPath
$auth = Get-STFAuthenticationService -StoreService $store
Note:
Note: The above configuration will work with the Receiver for Web

# Change this value for your Store
$storeVirtualPath = '/Citrix/Store1'
$auth = Get-STFAuthenticationService -Store (Get-STFStoreService -VirtualPath $storeVirtualPath)
$spId = $auth.AuthenticationSettings['samlForms'].SamlSettings.ServiceProvider.Uri.AbsoluteUri
$acs = New-Object System.Uri $auth.Routing.HostbaseUrl, ($auth.VirtualPath + '/SamlForms/AssertionConsumerService')
$md = New-Object System.Uri $auth.Routing.HostbaseUrl, ($auth.VirtualPath + '/SamlForms/ServiceProvider/Metadata')
$samlTest = New-Object System.Uri $auth.Routing.HostbaseUrl, ($auth.VirtualPath + '/SamlTest')
Write-Host 'SAML Service Provider information:
Service Provider ID: $spId
Assertion Consumer Service: $acs
Metadata: $md
Citrix Workspace Single Sign On
Test Page: $samlTest' The sample output of the above command looks like this.
The sample output of the above command looks like this.SAML Service Provider information:
Service Provider ID: https://storefront.example.com/Citrix/StoreAuth
Assertion Consumer Service: https://storefront.example.com/Citrix/StoreAuth/SamlForms/AssertionConsumerService
Metadata: https://storefront.example.com/Citrix/StoreAuth/SamlForms/ServiceProvider/Metadata
Test Page: https://storefront.example.com/Citrix/StoreAuth/SamlTest
Okta Configuration:
- On the Okta create a new application for the Web Platform with SAML 2.0 enabled.
- Once the new application is created follow the below steps to configure the SAML settings
Note:

- The Single Sign On URL in the above step should be the Assertion Consumer Service URL from the StoreFront Output.
- The Audience URI should be the Service Provider ID from the Storefront Output.
- Rest of the setting can be default.
- In the next step you can Preview the SAML assertion click on the link shown up in the below image.
- On the next step click on finish to the Service Provider configuration on the Okta.
- In the next step, click on the Sign On tab and edit the application user format to reflect AD User Principle Name
- Also click on the Identity Provider Metadata to download the metadata file which we will use in the Storefront Configuration steps below.
- In the next step assign the users to application on the Okta who will go through Okta to Storefront.
Storefront Configuration:
- On the Storefront, enable the SAML Authentication under the Manage Authentication Methods in the Storefront Console.
- Open an elevate PowerShell and run the below command to import the Okta metadata file.
Get-Module 'Citrix.StoreFront*' -ListAvailable | Import-Module
# Remember to change this with the virtual path of your Store.
$StoreVirtualPath = '/Citrix/Store'
Okta Remember Me
$store = Get-STFStoreService -VirtualPath $StoreVirtualPath
$auth = Get-STFAuthenticationService -StoreService $store
Okta Citrix Cloud
Okta Saas
Update-STFSamlIdPFromMetadata -AuthenticationService $auth -FilePath 'File path of the metadata file you downloaded from Okta'Note:
- Change this value for your Store.
- Also point the file path to the location where you saved the Okta metadata file.
- Now when you go to the Storeweb, you should get redirected to the Okta page for sign in.
Note: The above configuration will work with the Receiver for Web
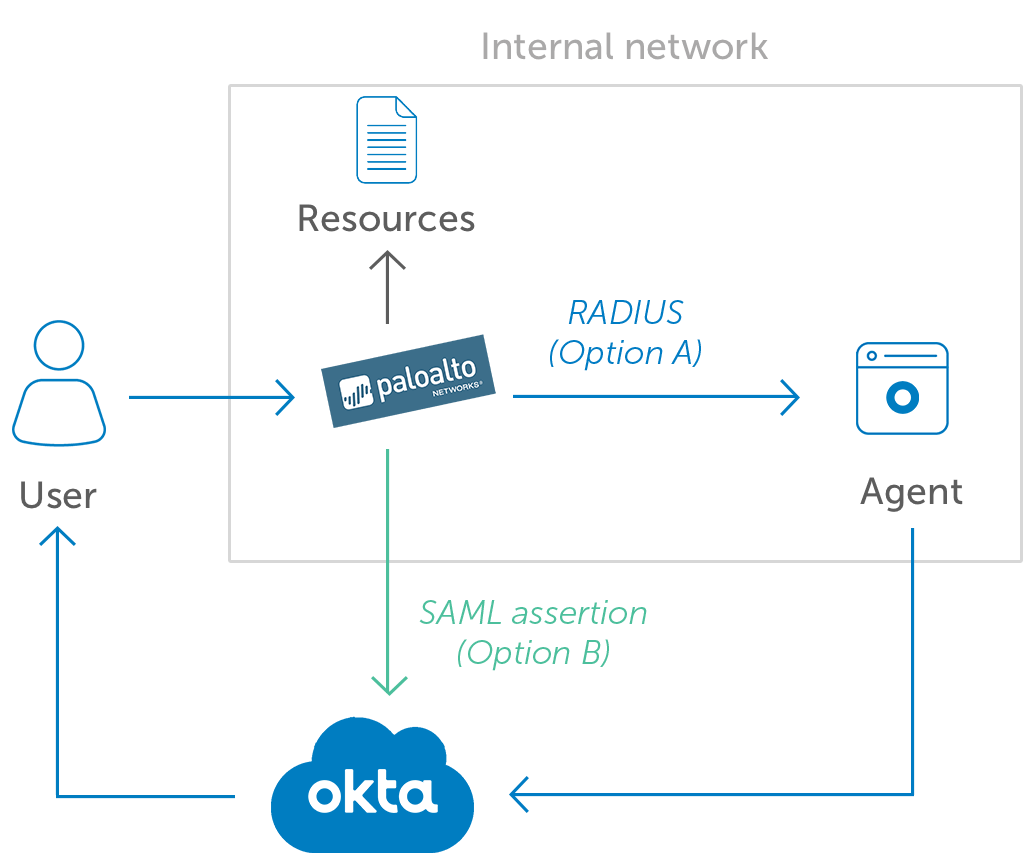
Citrix Cloud Gateway As Idp
Additional Resources
Citrix Cloud And Okta
References for Configuring FAS:
https://docs.citrix.com/en-us/xenapp-and-xendesktop/7-12/secure/federated-authentication-service.html
Disclaimer
Citrix is not responsible for and does not endorse or accept any responsibility for the contents or your use of these third party Web sites. Citrix is providing these links to you only as a convenience, and the inclusion of any link does not imply endorsement by Citrix of the linked Web site. It is your responsibility to take precautions to ensure that whatever Web site you use is free of viruses or other harmful items.
