Cisco Meraki’s unique auto provisioning site-to-site VPN connects branches securely, without tedious manual VPN configuration. Leveraging the power of the cloud, MX Security Appliances configure, monitor, and maintain your VPN so you don't have to.
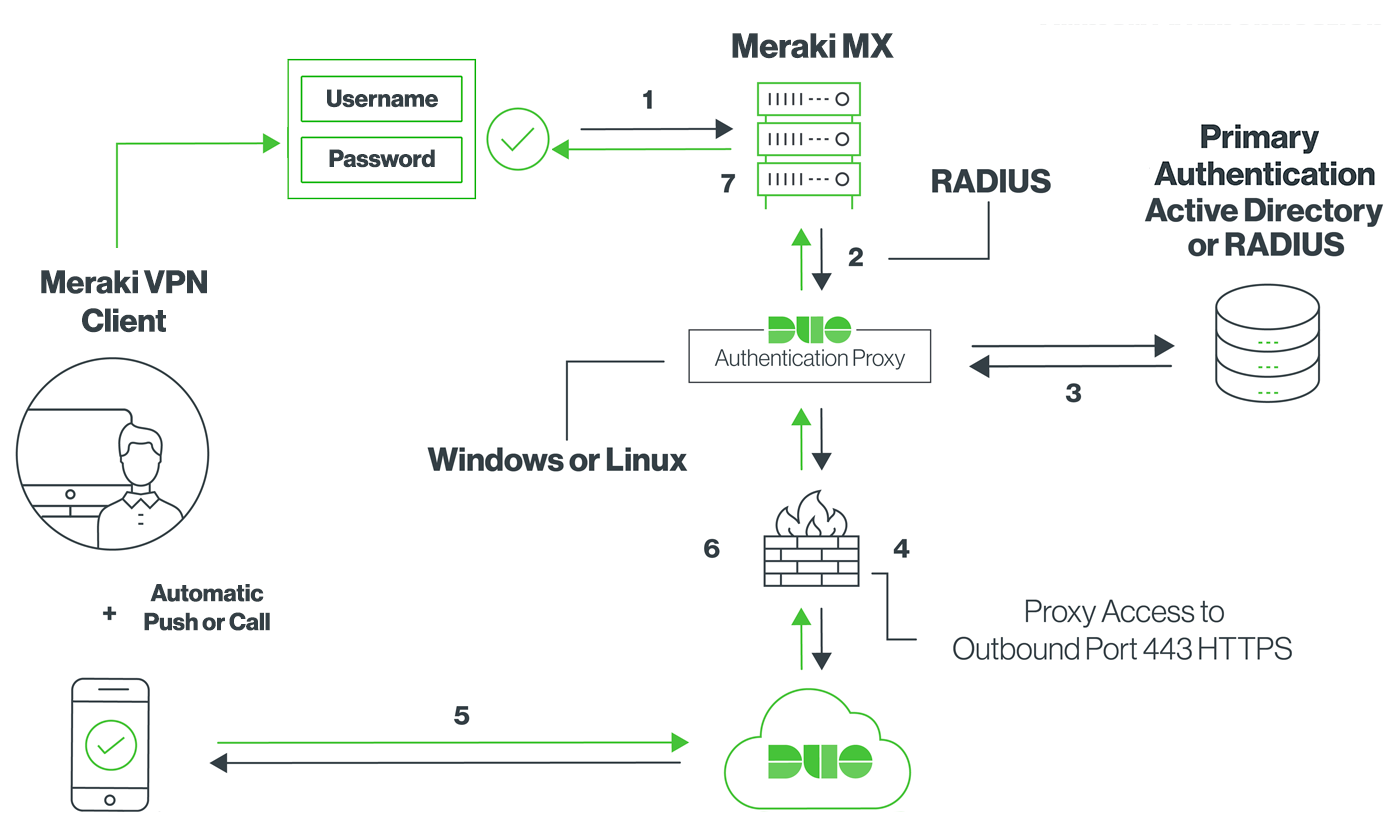
We are looking at moving to a Meraki MX-250 Security Device. I have a VPN tunnel with another Company. I believe they have a Juniper VPN Device, we have a server they connect to over a the VPN tunnel today. The Servers Private IP is 172.18.0.99. They require us to Nat the server to a public IP sa. Meraki Client VPN uses the Password Authentication Protocol (PAP) to transmit and authenticate credentials. PAP authentication is always transmitted inside an IPsec tunnel between the client device and the MX security appliance using strong encryption.
Meraki Firewall Ssl Vpn
Cisco Meraki’s unique auto provisioning site-to-site VPN connects branches securely with complete simplicity. Using IPsec over any wide area network, the MX links your branches to headquarters as well as to one another as if connected with a virtual Ethernet cable. Customers accessing or moving services to the Amazon Web Services cloud can use Auto VPN to connect directly to a virtual MX inside their Virtual Public Cloud.


MX Security Appliances automatically configure VPN parameters needed to establish and maintain VPN sessions. A unique cloud-enabled hole-punching and discovery mechanism enables automatic interconnection of VPN peers and routes across the WAN, and keeps them updated in dynamic IP environments. Security associations and phases, authentication, key exchanges, and security policies are all handled automatically by MX VPN peers. Site-to-site connectivity is established through a single click in the Cisco Meraki dashboard. Intuitive tools built in to the Cisco Meraki dashboard give administrators a real-time view of VPN site connectivity and health. Round trip time latency between peers and availability status information automatically keep track of all the VPN peers in the network.
Flexible tunneling, topology, and security policies
Configurations for split-tunneling and full-tunneling back to a concentrator at headquarters are fully supported and configured in a single click. Hub-and-spoke and full mesh VPN topologies give deployment flexibility, and a built-in site-to-site firewall enables custom traffic and security policies that govern the entire VPN network.
Meraki Firewall Vpn Download
Cloud Managed Security Appliances
Meraki Vpn Firewall Rules
See features, specifications, and pricing for Cloud Managed Security Appliances.